OverTheWire-Bandit 1-27
官网:http://overthewire.org/wargames/bandit/
强盗战争是针对绝对的初学者。它将教授需要能够玩其他战争游戏的基础知识,通过这个游戏能学习到很多Linux的基础知识。和大多数其他游戏一样,这个游戏按层次组织。你从0级开始尝试“击败”或“完成”它。完成一个关卡会产生关于如何开始下一关的信息。本网站上的“Level
这个游戏有27关,对应27对账号密码组合。开始的时候送我们一个第一关的账号密码:「bandit0」-「bandit0」。
我们需要使用这个账号登陆服务器并找到「bandit1」的密码,然后使用得到的密码登陆「bandit1」,再找到「bandit2」的密码……
Level 0
这个级别的目标是让你使用SSH登录游戏。您需要连接的主机是 bandit.labs.overthewire.org,端口2220.用户名是bandit0,密码是bandit0。登录后,进入1级页面,了解如何击败1级。
我用的是XShell直接按提示输入账号密码,连接成功,进入下一级
Level 0 → Level 1
描述:下一级别的密码存储在位于主目录中的名为readme的文件 中。使用此密码使用SSH登录bandit1。只要你找到一个级别的密码,使用SSH(在端口2220)登录到该级别,并继续游戏。
过程:
1 | bandit0@bandit:~$ ls |
ls命令列出当前目录下的文件,而用cat命令查看文件内容
密码:boJ9jbbUNNfktd78OOpsqOltutMc3MY1
Level 1 → Level 2
用账号:bandit1 ,密码:boJ9jbbUNNfktd78OOpsqOltutMc3MY1进入本关
描述:下一级的密码存储在一个名为- ,位于主目录中的文件中
过程:
1 | bandit1@bandit:~$ ls |
文件名是:”-“,如果是其他名字直接 cat filename 就行了,如果是 “cat - “的话,就有一些小问题,因为 bash 中会用”-“来接受命令行参数,未避免冲突,我们使用”./“来表示当前目录,那”-“文件就表示为”./-“。
密码:CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
Level 2→ Level 3
用账号:bandit2 ,密码:CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9进入本关
描述:下一级别的密码存储在位于主目录中的文件名为spaces in this filename
过程:
1 | bandit2@bandit:~$ ls |
“ls”查看文件,注意spaces in this filename是一个文件,而不是四个,虽然文件名存在空格,但是Linux有自动补全的功能,输入”cat s”后,按一下Tab键就自动补全了
密码:UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
Level 3 → Level 4
用账号:bandit3 ,密码:UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK进入本关
描述:下一级别的密码存储在inhere目录中的隐藏文件中 。
过程:
1 | bandit3@bandit:~$ ls |
“ls -a”显示所有文件及目录 (ls内定将文件名或目录名称开头为”.”的视为隐藏档,不会列出),”.”开头的文件为隐藏文件,故”ls”没有列出
密码:pIwrPrtPN36QITSp3EQaw936yaFoFgAB
Level 4→ Level 5
用账号:bandit4 ,密码:pIwrPrtPN36QITSp3EQaw936yaFoFgAB进入本关
描述:下一级别的密码存储在inhere目录中唯一的人类可读文件中。提示:如果你的终端搞砸了,试试“重置”命令。
过程:
1 | bandit4@bandit:~$ ls |
inhere文件夹中存在10个文件,用Linux的”file”命令辨识文件类型,”*”是通配符,只有”-file07”文件类型不一样,八九不离十就是它了。
密码:koReBOKuIDDepwhWk7jZC0RTdopnAYKh
Level 5→ Level 6
用账号:bandit5,密码:koReBOKuIDDepwhWk7jZC0RTdopnAYKh进入本关
描述:下一级别的密码存储在inhere目录下的某个文件中,并具有以下所有属性:人类可读,大小为1033字节,不可执行
过程:
1 | bandit5@bandit:~$ ls |
“ls -l”除文件名称外,亦将文件型态、权限、拥有者、文件大小等资讯详细列出,发现有很多文件夹,”find . -type f -size 1033c”,”.”查找当前目录以及子目录,-type f指定文件类型为普通文件,-size 1033c指定文件大小为 1033 bytes
密码:DXjZPULLxYr17uwoI01bNLQbtFemEgo7
Level 6→ Level 7
用账号:bandit6,密码:DXjZPULLxYr17uwoI01bNLQbtFemEgo7进入本关
描述:下一级别的密码存储在服务器的某个位置,并具有以下所有属性:由用户bandit7拥有,由groupitit6拥有,大小为33个字节
过程:
1 | bandit6@bandit:~$ find / -group bandit6 -user bandit7 -size 33c 2>/dev/null |
“/“ linux 根目录,从最顶层开始查找,”2>/dev/null”中”2”表示错误输出,”>”是重定向符号表示把信息送到哪里,”/dev/null”是Linux黑洞.
密码:HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
Level 7→ Level 8
用账号:bandit7,密码:HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs进入本关
描述:下一级的密码存储文件data.txt中, “millionth” 的下一个单词。
过程:
1 | bandit7@bandit:~$ ls |
命令讲解”grep match_pattern file_name” ,在文件中搜索一个单词,命令会返回一个包含“match_pattern”的文本行
密码:cvX2JJa4CFALtqS87jk27qwqGhBM9plV
Level 8→ Level 9
用账号:bandit8,密码:cvX2JJa4CFALtqS87jk27qwqGhBM9plV进入本关
描述:下一级别的密码存储在文件data.txt中, 并且是仅出现一次的唯一文本行
过程:
1 | bandit8@bandit:~$ ls |
sort命令用于将文本文件内容加以排序,可针对文本文件的内容,以行为单位来排序。”uniq -u”是上下相邻两行对比得到是否为单一行。
密码:UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
Level 9→ Level 10
用账号:bandit9,密码:UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR进入本关
描述:下一级别的密码存储在文件data.txt 中的少数人类可读字符串之一中,以几个’=’字符开始。
过程:
1 | bandit9@bandit:~$ ls |
strings是在文件中查找可打印字符串并输出长度为4个或更多的字符串,遇到换行或空字符结束,用 grep 命令筛选 含有”==”的字符串。
密码:truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
Level 10→ Level 11
用账号:bandit10,密码:truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk进入本关
描述:下一级的密码存储在包含base64编码数据的文件data.txt中
过程:
1 | bandit10@bandit:~$ ls |
base64 编码了数据,解码就好了
密码:IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
Level 11→ Level 12
用账号:bandit11,密码:IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR进入本关
描述:下一级的密码存储在文件data.txt中,其中所有小写(az)和大写(AZ)字母已被旋转了13个位置
过程:
1 | bandit11@bandit:~$ ls |
tr 命令,参数为两个字符集,把第一个字符集中的字符替换为第二个字符集中的对应字符。题目中说旋转了13个位置,相当于26个字母前十三个和后十三个换了个位置。按照这样的对应关系,调整给出的字符集。
密码:5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
Level 12→ Level 13
用账号:bandit12,密码:5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu进入本关
描述:下一级的密码存储在data.txt文件中,该文件是一个经过反复压缩的文件的十六进制转储文件。对于这个级别,可以在/ tmp下创建一个可以使用mkdir工作的目录。例如:mkdir / tmp / myname123。然后使用cp复制数据文件,并使用mv重命名它。
过程:
1 | bandit12@bandit:~$ ls |
其实这一题并不是很难,一步一步看解题过程就明白怎么回事了,文件最开始是16进制,用” xxd -r”将16进制文件转换为二进制文件,然后每一步都查看一次文件类型,并重命名为相应的文件类型,主要运用”bzip2 -d”,”gzip -d”,”tar -xvf”以及`这些解压方法。
密码:8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
Level 13→ Level 14
用账号:bandit13,密码:8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL进入本关
描述:下一级的密码存储在 / etc / bandit_pass / bandit14中,只能由用户bandit14读取。对于这个级别,你不会得到下一个密码,但你得到一个私人SSH密钥,可以用来登录到下一个级别。 注意: localhost是指您正在使用的机器的主机名
过程:
1 | bandit13@bandit:~$ ls |
通过ssh命令,通过sshkey.private密钥连接进去,这里连接时不用指定端口(亲测),然后已经告诉你密码存在的位置,用cat查看
密码:4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Level 14→ Level 15
用账号:bandit14,密码:4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e进入本关
描述:可以通过将当前级别的密码提交到本地主机上的端口30000来检索下一级别的密码。
过程:
1 | bandit14@bandit:~$ nc localhost 30000 |
直接通过nc连接本地的30000端口,输入当前级别的密码后返回下一级密码。
密码:BfMYroe26WYalil77FoDi9qh59eK5xNr
Level 15→ Level 16
用账号:bandit15,密码:BfMYroe26WYalil77FoDi9qh59eK5xNr进入本关
描述:可以通过使用SSL加密将当前级别的密码提交到本地主机上的端口30001来检索下一级别的密码。
过程:
1 | bandit15@bandit:~$ openssl s_client -connect localhost:30001 -ign_eof |
使用openssl命令连接成功后复制上本关的密码回车即可获得下一关的密码。
密码:cluFn7wTiGryunymYOu4RcffSxQluehd
Level 16→ Level 17
用账号:bandit16,密码:cluFn7wTiGryunymYOu4RcffSxQluehd进入本关
描述:可以通过将当前级别的密码提交给本地主机上的端口(范围在31000到32000)来检索下一级的凭证。首先找出哪些端口有一个服务器监听它们。然后找出哪些人说SSL和哪些不。只有一台服务器可以提供下一个凭证,其他人只需发送给您即可发送给它。
过程:
1 | bandit16@bandit:~$ nmap -p 31000-32000 localhost |
后来才知道密码位于/etc/bandit_pass/bandit17
密码:xLYVMN9WE5zQ5vHacb0sZEVqbrp7nBTn
Level 17→ Level 18
此题接着上一题的shell
描述:homedirectory中有2个文件:passwords.old和passwords.new。下一级别的密码位于 passwords.new中,是密码.old和passwords.new之间已更改的唯一行。
过程:
1 | bandit17@bandit:~$ ls |
密码:kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd
Level 18→ Level 19
用账号:bandit18,密码:kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd进入本关
描述:下一级别的密码存储在家庭目录中的文件自述文件中。不幸的是, 当你使用SSH登录时,有人修改了.bashrc将你注销。
过程:
1 | Enjoy your stay! |
刚刚连进去就断开了
1 | bandit17@bandit:~$ ssh bandit18@localhost cat readme |
在进行ssh连接的时候就把参数带进去,在password: 后粘贴本关的密码后,就返回了下一关的密码。
密码:IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
Level 19→ Level 20
用账号:bandit19,密码:IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x进入本关
描述:要访问下一级,您应该使用homeu目录中的setuid二进制文件。执行它没有参数找出如何使用它。使用setuid二进制文件后,可以在通常的地方(/ etc / bandit_pass)找到该级别的密码。
大致意思就是告诉你 Home 目录下有个文件,先不带参数执行一下,他会告诉你怎么用。
过程:
1 | bandit19@bandit:~$ ls |
一步一步就知道这个文件的作用以及用法
密码:GbKksEFF4yrVs6il55v6gwY5aVje5f0j
Level 20→ Level 21
用账号:bandit20,密码:GbKksEFF4yrVs6il55v6gwY5aVje5f0j进入本关
描述:homedirectory中有一个setuid二进制文件,它执行以下操作:它在您指定为命令行参数的端口上连接到localhost。然后它从连接中读取一行文本,并将其与前一级别的密码(bandit20)进行比较。如果密码正确,它将传输下一级密码(bandit21)。
注意:尝试连接到您自己的网络守护程序,以查看它是否按照您的想法工作,这个程序会访问 localhost 的[你提供的端口号]来获取数据。这里我们需要处理两件事情:1.运行这个程序。2.创建一个监听事件并会回复这个程序当前关的密码。
过程:
首先使用nc 监听一个端口,并推送/etc/bandit_pass/bandit20文件内容,即bandit20的密码
1 | bandit20@bandit:~$ ls |
此时2333端口处于监听状态,再建立一个ssh连接
1 | bandit20@bandit:~$ ls |
成功读取到文件以后,就把下一关的密码发送到监听端口
1 | bandit20@bandit:~$ ls |
成功获得密码 。
密码:gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
Level 21→ Level 22
用账号:bandit21,密码:gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr进入本关
描述:一个程序从cron(基于时间的作业调度程序)定期自动运行 。查看/etc/cron.d/中的配置并查看正在执行的命令。
过程:
1 | bandit21@bandit:~$ cd /etc/cron.d/ |
cron指Linux系统下一个自动执行指定任务的程序(计划任务),” bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null” 中的”“表示每分钟执行一次这个脚本,再用cat查询该脚本的内容,不停把/etc/bandit_pass/bandit22文件内容(即下一关的密码)写入/tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv,并且更改了权限。
密码:Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
Level 22→ Level 23
用账号:bandit22,密码:Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI进入本关
描述:一个程序从cron(基于时间的作业调度程序)定期自动运行 。查看/etc/cron.d/中的配置并查看正在执行的命令。
注意:查看其他人编写的shell脚本是非常有用的技巧。这个级别的脚本有意使其易于阅读。如果您在理解它的功能时遇到问题,请尝试执行它以查看它打印的调试信息。
过程:
1 | bandit22@bandit:~$ cd /etc/cron.d |
直接赋值执行。
密码:jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n
Level 23→ Level 24
用账号:bandit23,密码:jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n进入本关
描述:一个程序从cron(基于时间的作业调度程序)定期自动运行 。查看/etc/cron.d/中的配置并查看正在执行的命令。
注意:此级别要求您创建自己的第一个shell脚本。这是非常大的一步,当你击败这个级别时,你应该为自己感到自豪!
注2:请记住,你的shell脚本一旦被执行就被删除,所以你可能想保留一份副本……
过程:
1 | bandit23@bandit:~$ cd /etc/cron.d |
在/tmp/文件夹中创建一个目录。创建一个shell脚本将/etc/bandit_pass /bandit24复制到我们的/tmp/文件夹。将shell脚本复制到/var/spool/bandit24/。给shell脚本和/tmp/文件夹适当的权限。/usr/bin/cronjob_bandit24.sh这个shell的作用就是执行 /var/spool/bandit24 的脚本,60s 如果还没之行结束会强制kill掉,然后删除。所以我们写了一个把 /etc/bandit_pass/bandit24/ 输出到 /tmp/crayon的脚本到这个目录下,然后付了个权限。
密码:UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ
Level 24→ Level 25
用账号:bandit24,密码:UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ进入本关
描述:守护进程正在端口30002上侦听,并且如果给出bandit24的密码和一个秘密的数字4位pincode,它会给你bandit25的密码。没有办法检索pincode,除非通过所有10000个组合,称为暴力。
过程:
1 | bandit24@bandit:~$ nc localhost 30002 |
大概就是要写一个脚本了,10000种组合
1 | bandit24@bandit:~$ clear |
生成一个名为crayon.txt的字典
1 | UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0001 |
1 | bandit24@bandit:/tmp/crayon$ nc localhost 30002 < /tmp/crayon/crayon.txt > /tmp/crayon/password.txt |
密码:uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG
Level 25→ Level 26
用账号:bandit25,密码:uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG进入本关
描述:从bandit25登录bandit26应该相当简单…用户bandit26的shell不是/ bin / bash,而是别的。了解它是什么,它是如何工作的以及如何摆脱它。
过程:
1 | bandit25@bandit:~$ ls |
刚连上去就被关闭了。
1 | bandit25@bandit:~$ cat /etc/passwd | grep bandit26 |
more 命令是一次显示一屏文字,然后左下角会显示一个 more 和当前显示了百分之多少, 之前在其他登陆中不曾见过,想必就是 more 命令显示的 text.txt 的内容,因为行数足以一屏显示完,所以没有显示 more 就没有显示,我们的思路就在 more 的这个特点上。我们要让他卡在一屏读不完的位置,也就是让你的终端高度读不下6行(字符画高度), 这样我们可以在 more 的状态下通过一些特性执行命令找到我们下一关的密码
先把窗口缩到足够小,然后通过密钥连接
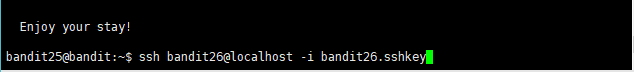
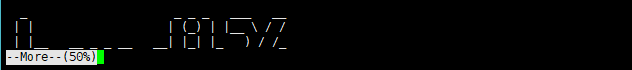
看到More后按V进入编辑模式

然后使用命令 :ex! /etc/bandit_pass/bandit26 打开我们需要的密码文件
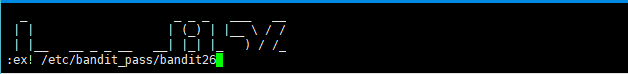
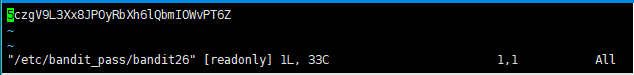
只想说长知识了,没想到还能这么玩
密码:5czgV9L3Xx8JPOyRbXh6lQbmIOWvPT6Z
Level 26 → Level 27
27级还不存在
gameover。。。。。。
有问题请留言